2025-9-9 12:03 |
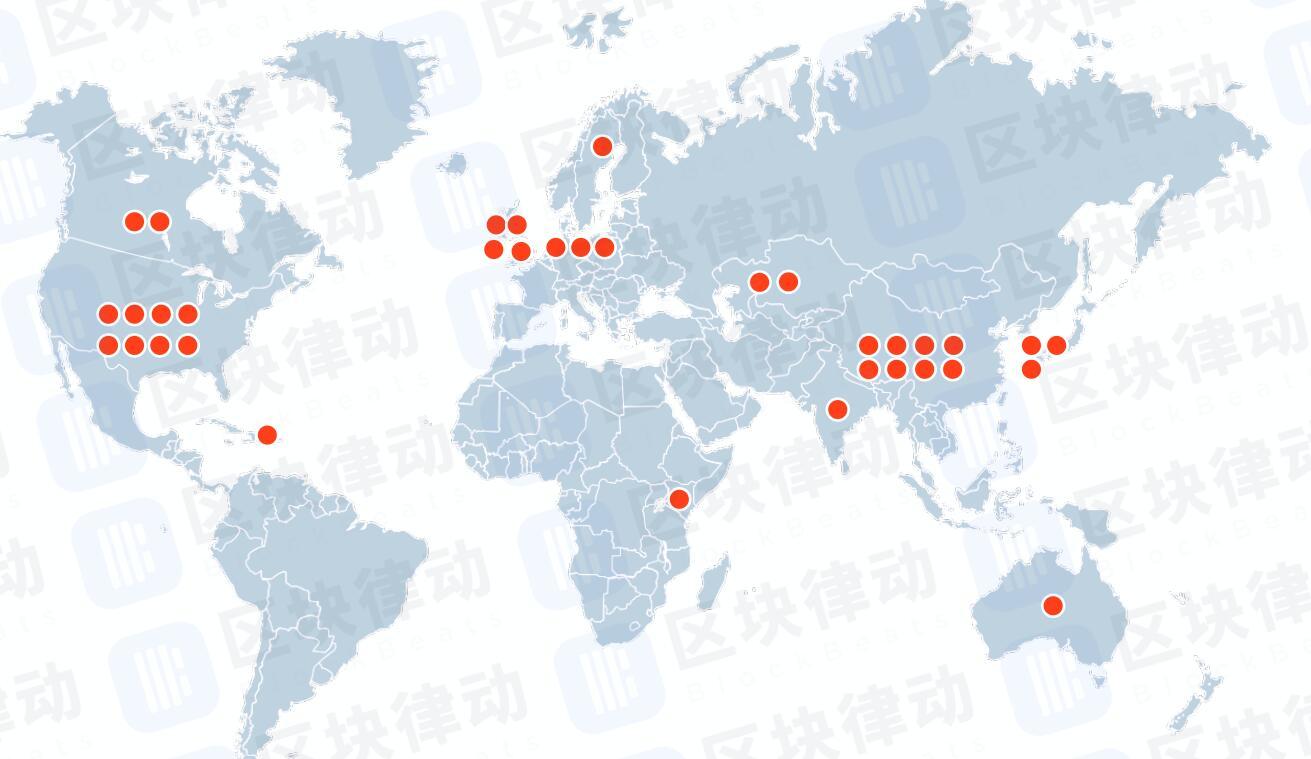
A major supply chain attack has rocked the crypto ecosystem, threatening users globally. Ledger’s CTO Charles Guillemet is sounding the alarm, urging caution and hardware wallet use. The attack, which began with a hacked Node Package Manager (NPM) account, has… origin »
Bitcoin price in Telegram @btc_price_every_hour
Supply Shock (M1) на Currencies.ru
|
|