Новости о Malware Discovered [ Фото новости ] [ Свежие новости ] | |
Hackers Are Using Malware to Infect Each Other’s Tools: Report
A security researcher at Cybereason recently discovered a new malware campaign in which hacking groups are targeting each other by infecting popular hacking tools. A recently discovered malware campaign has revealed quite an interesting development, suggesting that hackers themselves are becoming the targets of their peers. дальше »
2020-3-11 10:15 | |
|
|
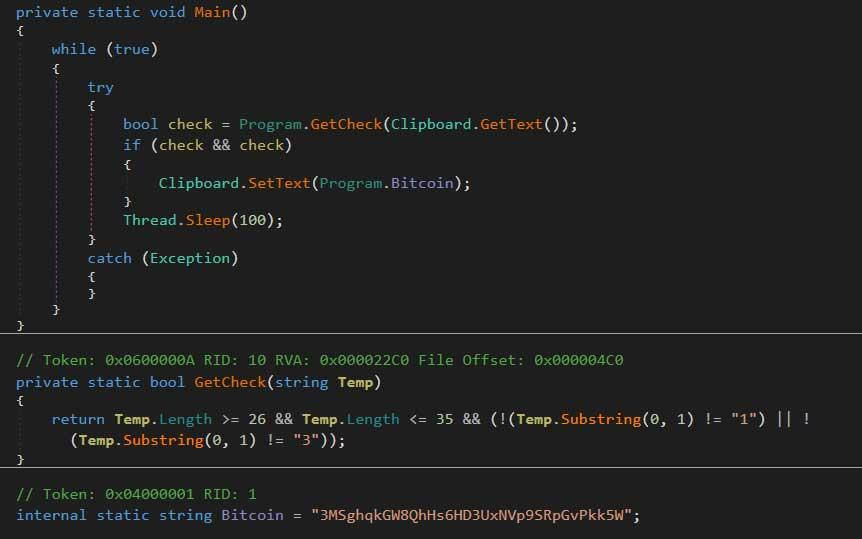
Hackers are Stealing Crypto Using Clipper Malware
Hackers can steal crypto payments by using a relatively new malware that replaces the receiving address between copying and pasting. Don’t CTRL+C CTRL +V According to a report from February of this year, a security researcher called Lukas Stefanko discovered that hackers had brought the so-called Clipper Malware to Google Play via infected cryptocurrency apps. дальше »
2019-12-4 12:16 | |
|
|
New cryptomining malware uses WAV audio files to conceal its tracks
A new campaign discovered by security researchers shows that cybercriminals are hiding malware inside WAV audio files. This technique of obfuscating malicious code in plain sight — a method called steganography — was uncovered by BlackBerry’s cybersecurity subsidiary Cylance. дальше »
2019-10-17 14:00 | |
|
|
New Crypto-Jacking Malware ‘Graboid’ Infects Thousands of Computers to Mine Monero (XMR)
Palo Alto Networks’ Unit 42 researchers discovered a new crypto-jacking malware that infected over 2000 victim's computers. The malware infects unsuspecting users’ computers to mine Monero (XMR), a privacy-based cryptocurrency. дальше »
2019-10-17 00:37 | |
|
|
Researchers find Bitcoin sextortion malware also mines Monero
Analysts have reportedly discovered the source of the sextortion emails that’ve plagued the internet since last year — the ones that demand Bitcoin or else they’ll leak videos of you masturbating to kinky pornography. дальше »
2019-10-14 18:12 | |
|
|
Cybercriminals are targeting healthcare companies with phishing campaigns to steal sensitive data
Healthcare providers are facing an unprecedented level of social engineering-driven malware threats, according to new research. The findings — disclosed by California-based enterprise security solutions provider Proofpoint US — discovered at least 77 percent of email attacks on the medical sector during the first three months of 2019 involved the use of malicious links. дальше »
2019-10-9 19:00 | |
|
|
Newly Discovered Spyware Uses Telegram Bots to Steal Cryptocurrency from a Number of Wallets
Jupiter Threat Labs recently released a report about a newly discovered commercial spyware called “Masad Clipper and Stealer.” It uses Telegram bots as its command and control (C2) to phish information from Windows and Android users, along with the capability to steal cryptocurrency from unsuspecting victims, while dumping more malware on their devices. The report […] дальше »
2019-9-28 00:30 | |
|
|
Trojan Virus Discovered That Steals Password Data from Crypto Wallets
Cybercriminals have launched a new malware conceived to steal data from crypto wallets. ThreatLabZ, a Zscaler team of security experts, has identified the malware as a RAT (Remote Access Trojan), which they named InnfiRAT. дальше »
2019-9-19 20:00 | |
|
|
New Linux Malware Mines Cryptos By Using Backdoor: Latest TrendMicro Research
For a long time, Linux users were happy to be free of most malware. Unfortunately, we have been seeing some malware focused on them lately. The latest threat was discovered by TrendMicro and it is called Skidmap. дальше »
2019-9-17 03:00 | |
|
|
Nasty Glupteba malware uses Bitcoin blockchain to keep itself alive
Cybersecurity researchers have discovered a new strain of the nefarious Glupteba malware that uses the Bitcoin blockchain to ensure it remains dangerous. TrendMicro’s latest blog details the previously undocumented variant which is capable of invading systems to mine Monero cryptocurrency and steal sensitive browser data like passwords and cookies. дальше »
2019-9-4 17:09 | |
|
|
Google researchers reveal data-stealing, web-based iPhone exploit that was active for years
Researchers from Google have uncovered what appears to be a concentrated malware campaign targeting iPhones for at least two years. Thankfully, this may be over now, although they warn it’s possible there are others that are yet to be seen. дальше »
2019-8-30 10:02 | |
|
|
Programmer Discovers Cryptojacking Malware on GitHub
Juskoljo, a GitHub user who has eight repositories on the platform, has discovered malicious cryptojacking malware in 11 code libraries for the Ruby programming language. The libraries containing the deadly malware have reportedly been downloaded nearly four thousand times, according to reports on August 21, 2019. дальше »
2019-8-23 23:00 | |
|
|
Open-source spyware bypasses Google Play defenses — twice
Google Play Store continues to attract sketchy Android apps despite its best efforts to vet incoming apps for malware. In a new report published by security firm ESET, researchers have discovered the first known instance of an open-source spyware bypassing the internet giant’s app store vetting process — twice. дальше »
2019-8-22 15:57 | |
|
|
Report: Researchers Discover New Cryptojacking Malware for Mining Monero
Varonis, a data security and analytics company, has discovered new strains of cryptojacking malware that hijacks a victim’s computer resources to mine monero (XMR), and a mysterious web shell while investigating the cause of a cryptomining infection for a client. дальше »
2019-8-15 19:00 | |
|
|
This spooky Monero-mining malware waits to be controlled remotely
Cybersecurity researchers have discovered a mysterious new strain of cryptocurrency mining (cryptomining) malware that employs powerful techniques to avoid detection and analysis. Software firm Varonis determined the malware is based on Monero mining software XMRig, which is open source and hosted on GitHub. дальше »
2019-8-15 23:42 | |
|
|
Researchers discover malware that records users’ screens when they watch porn
Researchers from antivirus developer ESET recently discovered a new form of spam-delivered malware that threatens to steal unsuspecting users’ passwords and financial information, and record their screens if they watch pornography. дальше »
2019-8-15 23:19 | |
|
|
Bad Actors Hijack Ukraine’s Government System to Mine Monero
Hackers have planted cryptocurrency mining malware on the computers of the Ukrainian State Judicial Administration (SJA), secretly minting privacy-centric monero (XMR) altcoin for over six months, reports Finance Magnates on June 24, 2019. дальше »
2019-6-25 21:00 | |
|
|
Russian Hackers May Be Responsible for Coincheck Heist
Investigators looking into the more than half a billion dollar Coincheck heist of 2018 have revealed that Russian hackers may have been responsible for the attack. Reports indicate that two malicious malware written in Russian, “mokes and “netwire,” have been discovered in the previously hacked Coincheck employee’s computer. дальше »
2019-6-20 13:00 | |
|
|
Report: Android Phishing Malware Impersonates Turkish Cryptocurrency Exchange
Malware discovered by ESET is reportedly masquerading as Turkish crypto exchange BtcTurk to phish for login credentials
дальше »2019-6-18 18:42 | |
|
|
Trend Micro Claims Outlaw Hacking Group’s Botnet is Spreading Monero Malware Mining
The cybersecurity company Trend Micro says it has discovered a web address that is spreading a botnet featuring a Monero (XMR) mining component. The botnet was also bundled with a backdoor-based exploit. дальше »
2019-6-13 22:10 | |
|
|
Yet another cryptocurrency mining botnet caught targeting China
It seems we can’t go more than a week without news of a new cryptocurrency mining malware or botnet being discovered. This time, security researchers have uncovered another Monero mining botnet that’s targeting China. дальше »
2019-6-13 16:02 | |
|
|
BlackSquid Malware Exploiting Web Servers to Mine Monero (XMR)
Cybersecurity researchers have discovered BlackSquid, a new malware family that exploits unpatched loopholes in web servers, network drives, and removable drives to mine privacy-centric monero (XMR), according to a TrendMicro report on June 3, 2019. дальше »
2019-6-5 09:00 | |
|
|
Guardicore Labs: Turtlecoin (TRTL) Privacy Token at Heart of Cryptojacking Malware on 50,000 Servers
A recent analysis made by the cybersecurity group Guardicore Labs has discovered that as many as 50,000 servers around the world are currently infected with a malware that is being used for cryptojacking. дальше »
2019-5-29 22:10 | |
|
|
Criminals Raise the Stakes in Crypto Mining Malware Using Confluence Exploit Per Trend Micro Find
Cybercriminals are getting bolder and smarter all the time and it is hard to keep up with them, as they keep finding new exploits in several pieces of software. Now, it was recently discovered by the security intelligence company Trend Micro that the Confluence software, created by Atlassian, was used to spread crypto mining malware. […] дальше »
2019-5-8 02:30 | |
|
|
New Malware, Shellbot Revealed, with the Ability to Create Crypto Using Others’ Resources, Be Aware
On Wednesday, May 1, 2019, security-focused firm, Threat Stack disclosed the findings of a relatively new malware called Shellbot to TechCrunch. As per the claims made, Shellbot – which was first discovered on an unnamed US firm’s server – has the ability to infect computers with Linux servers that carry easy-to-break into passwords, and then […] дальше »
2019-5-2 01:53 | |
|
|
Mueller Report: Russia Used Bitcoin to Fund DNC Hacks
An intelligence branch of the Russian government used bitcoin to fund its cyberwarfare efforts to interfere with the 2016 U. S. presidential election, the Mueller Report claims. дальше »
2019-4-19 23:21 | |
|
|
Ukranian Hacker Caught Infecting His Own Websites with Crypto Malware
According to the Ukranian cyber police, an unnamed man infected a bunch of his websites with Wannacry-like malware. Police Search Reveals Intentional Infection An unreliable Google translation makes it sound as if the man’s home had been invaded and police were investigating when they discovered his activities. дальше »
2019-3-28 22:14 | |
|
|
Wasabi Wallet Developer Raises Alarm over Malware Masquerading as Wallet Site
Cryptocurrency scammers have created a fraudulent website that contains links to the popular Wasabi cryptocurrency wallet. However, Wasabi co-founder nopara73 discovered on March 21, 2019, that one of the links is actually malware that links Windows OS users to an entirely phony website. дальше »
2019-3-25 16:00 | |
|
|
Scam Emails and Clipboard Hijackers Proliferate to Pilfer Bitcoin
Receiving Bitcoin investment related emails could cause a Windows clipboard hijacker to be installed on your computer, researchers warn. The new malware spam campaign that aims to steal bitcoins from its victims is currently underway; it’s still unknown how many devices are affected. дальше »
2019-3-16 00:35 | |
|
|
First Case of Crypto-Jacking ‘Clipper’ Malware Found on Google Play Store
A new form of cryptocurrency-stealing malware has been identified in the Google Play store. Dubbed ‘clipper’ malware, it was discovered inside an app impersonating MetaMask—a full browser extension which allows Ethereum-based apps to run on a browser without running a full Ethereum node. дальше »
2019-2-12 11:12 | |
|
|
Warning: Imposter Apps Stealing Crypto from Unwitting Users
Malware researcher and cybersecurity expert, Lukas Stefanko just discovered something concerning in the Google Play store. Stefanko, who specializes in Android security found a MetaMask imposter that is designed to steal passwords or security phrases. дальше »
2019-2-12 01:04 | |
|
|
Google Play Store Caught Hosting Fake Metamask Crypto Malware
Crypto markets may still be way down but malware is on the rise and is still infiltrating the largest app market places on the web. Google Play Store has yet again been found to be hosting malicious applications designed to steal cryptocurrencies. дальше »
2019-2-11 11:01 | |
|
|
A New Malware on Apple Mac Uses Browser Cookies to Steal Cryptocurrencies
According to Palo Alto Networks’ Unit 42, a newly discovered malware which targets the Mac platform could be stealing browser cookies linked to cryptocurrency exchanges and wallet services used by its victims. дальше »
2019-2-5 13:44 | |
|
|
New Mac Malware Can Steal Crypto from Exchanges, Can it be Prevented?
Unit 42, the global threat intelligence team at Palo Alto Network, discovered Mac malware that can steal cookies linked to crypto exchanges and wallets. Although usernames and passwords may not be sufficient to initiate withdrawals at crypto exchanges, if hackers manage to steal a combination of login credentials, web cookies, authentication cookies, and SMS data, it could steal user funds. дальше »
2019-2-2 21:32 | |
|
|
New Anatova Cryptocurrency Malware Found Impersonating Apps, Stronger Than Ryuk Ransomware
New Crypto Malware Found Impersonating Apps A new crypto malware called Anatova has been discovered and according to researchers, has grave potential. One of the most important facts to note about this new malware is that it often tricks users into downloading them. дальше »
2019-1-24 23:52 | |
|
|
Watch out for this new cryptocurrency ransomware stalking the web
Researchers have discovered “Anatova”, a brand new family of cryptocurrency-fuelled ransomware, and they warn it has the potential to become outright dangerous. Cybersecurity firm McAfee explained Anatova hides in seemingly innocuous icon files – usually the same popular games or applications – in order to fool the user into downloading the malware. дальше »
2019-1-23 19:58 | |
|
|
Cryptocurrency mining malware has become self-aware (kinda)
A common form of cryptocurrency mining malware has evolved and is now able to switch off security services to continue mining without being detected. Security researchers at Palo Alto Networks’ Unit 42 discovered that the malware used by cryptojacking group “Rocke” is able to gain administrative privileges to Linux-based cloud servers and uninstall vital security programs. дальше »
2019-1-17 18:18 | |
|
|
Researchers Claim 400,000+ MikroTik Routers Infected With Mining Malware
MikroTik mining malware was first discovered in Brazil in August, but the virus continues to spread all over the world.
дальше »2018-12-7 23:50 | |
|
|
415,000 routers worldwide hijacked to secretly mine cryptocurrency
Researchers have discovered over 415,000 routers across the globe have been infected with malware designed to steal their computing power and secretly mine cryptocurrency. The attack, which is still ongoing, affects MikroTik routers in particular. дальше »
2018-12-4 20:38 | |
|
|
McAfee Labs Discovers New WebCobra Crypto Mining Malware From Russian Hackers To Mine Monero (XMR)
McAfee Labs is known for their protection software that has been highly popularized since consumers started using the internet. It should come as no surprise that their latest press release shows that they have discovered a new malware from cryptocurrency hackers. дальше »
2018-11-15 10:50 | |
|
|
McAfee Labs discovers Russian malware mining Monero (XMR) and Zcash (ZEC)
McAfee Labs researchers have discovered new Russian malware, dubbed WebCobra, which harnesses victims’ computing power to mine Monero (XMR) and Zcash (ZEC). “Coin mining malware is difficult to detect. дальше »
2018-11-14 16:49 | |
|
|
New Russian malware mines different cryptocurrency based on your system
Is your computer suddenly sluggish and hot all the time? You might have fallen victim to this new Russian malware designed to steal your computing power to secretly mine cryptocurrency. Researchers from McAfee labs have discovered a new breed of crypto-jacking malware which cannibalizes your computing power to mine Monero or Zcash. дальше »
2018-11-13 19:56 | |
|
|
Switzerland: Trojan horses are evolving to target cryptocurrency exchanges
A computer virus that mines the anonymous cryptocurrency Monero has been ranked as the sixth most significant malware to hit Switzerland in the first half of this year. Swiss researchers also discovered that cybersecurity threats once focused on breaking into online banking services have pivoted to more efficiently attack cryptocurrency exchanges. дальше »
2018-11-8 19:33 | |
|
|