2020-11-21 17:55 |
Between October 28 and November 18, Ledger Donjon—Ledger’s world-class team of security researchers—ran a unique Capture the Flag (CTF) competition, where security enthusiasts, experts, and researchers were challenged with finding the solution to an array of security problems that Ledger Donjon prepared.
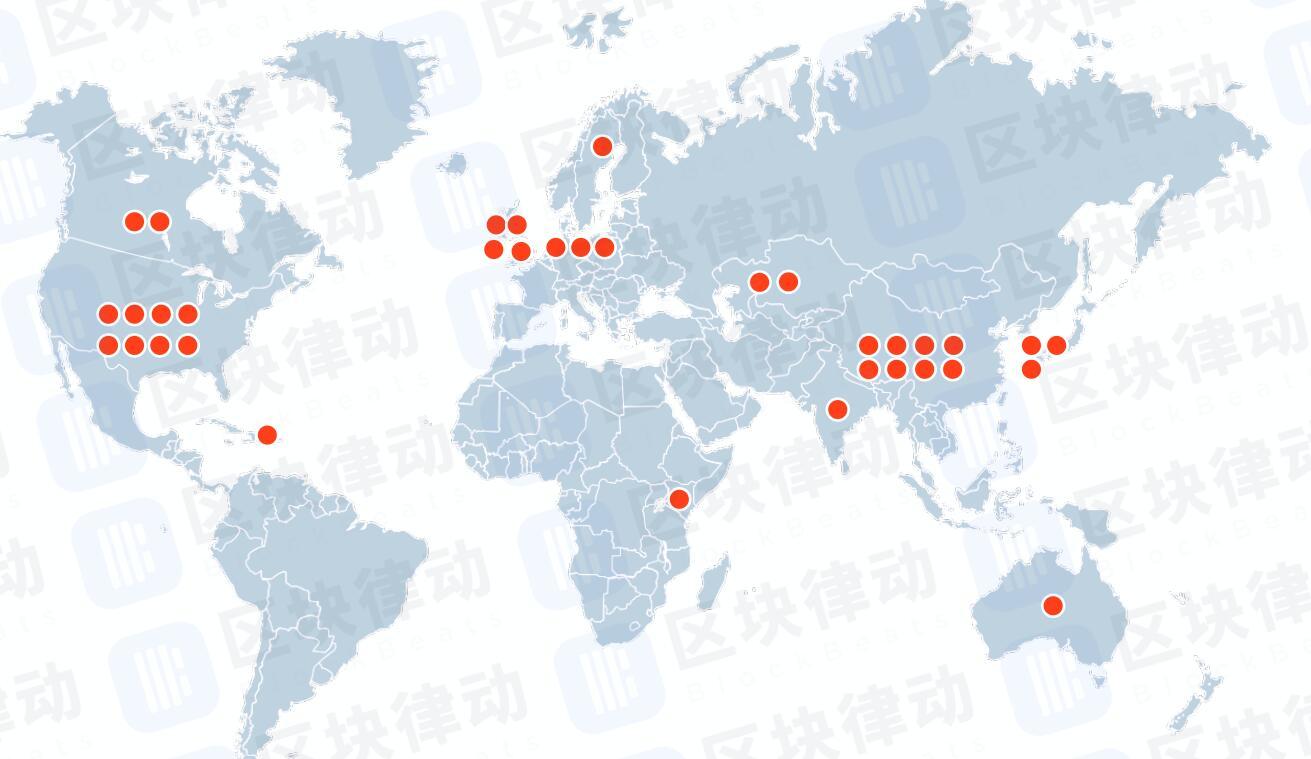
In total, more than 400 participants from around the world rose to the challenge of the Ledger CTF competition, many of which racked up an impressive score using their wits, guile, and knowledge to solve even the most fiendishly difficult challenges.
Here, we take some time to shed light on the goals of the Capture the Flag competition, and help to decipher some of its unique challenges. Stay glued until the end to find the list of Ledger CTF champions!
For the boldest experts, the CTF challenge is completely open-source, and can be freely replayed or modified. We will also publish a full list and breakdown of the solutions, as well as a link to the source code in the coming days.
What is a CTF?In the computer security industry, a Capture the Flag (CTF) challenge is a type of security competition where users attempt to discover flags (usually a string of text) hidden in purposefully-vulnerable programs. These flags can only be obtained by successfully exploiting the program by whatever means necessary.
These security CTF challenges vary in form and function but they all have one thing in common—they require skill, expertise, and creativity to solve.
Ledger’s CTF challenge took the form of a Jeopardy CTF. This essentially means players were tasked with solving a wide range of problems devised by Ledger, and would earn points for every correct solution. Like the popular TV show Jeopardy! These challenges covered a range of categories and the more difficult problems awarded more points—helping us test both the breadth of depth of each player’s knowledge!
In the case of the Ledger Donjon CTF, this was a three-week challenge covering 19 different security-related scenarios. Challengers could either work alone or as a team, and the ten challengers with the most flags (points) won a prize.
Why the Ledger Donjon CTF?Ledger Donjon’s team of world-class security experts and researchers work to bring trust and confidence to crypto owners by refining and hardening the security of Ledger products, and the crypto industry as a whole through its research.
This involves analyzing the security of prominent products throughout the crypto ecosystem, by identifying attack points that can then be fixed. Much of what Ledger Donjon publishes is open-source, including both attack tools and methodologies used, ensuring the benefits of this research can be carried forward to bolster the strength of the industry.
For example, in May 2020, Donjon was able to extract the PIN code from the ATECC508A secure memory used in the Coldcard Mk2 hardware wallet. Following responsible disclosure practices, this attack vector was reported to the manufacturers long before Donjon’s findings were made public.
With the goal of bringing transparency and openness to the crypto ecosystem, the Ledger Donjon 2020 CTF is designed to reproduce some of the real security issues that Donjon has encountered and resolved—helping crypto enthusiasts and developers alike get to grips with some of the work going on behind the scenes to keep the crypto industry secure.
Most of the challenges in this year’s CTF were completely original and directly related to blockchain, wallets, private keys, etc., helping participants get some hands-on experience with crypto-security challenges.
Decrypting 5 of the 19 ChallengesAt Ledger, we tried to cover every major base with this year’s CTF—covering a wide range of topics relevant to the crypto industry today.
Ranging from cryptographic vulnerabilities to side-channel and hardware-based attacks, this CTF was designed to test the knowledge and mettle of participants to see who has what it takes to capture the Ledger Fortress.
Here, we take a look into the rationale behind some of the more popular challenges, and discuss their implications in today’s crypto industry.
Category: CryptographyAs their name suggests, your private keys are designed to be kept private, since they allow you (or anyone who knows them) to unlock and spend the funds they control access to. These private keys take the form of a long series of numbers and letters.
Normally, private keys are generated using a Random Number Generator (RNG) to ensure they are as close to random as possible. As a result, the resulting private key is normally too random to guess (or brute-force), keeping your coins safe… Normally.
This CTF challenge tasks participants with exploiting the weaknesses of an RNG used by some existing crypto-security solutions. To pass the challenge, participants must correctly predict the private key the RNG would generate.
RNGs are critical to the security of cryptocurrency wallets since flawed RNGs can produce insecure (non-random) private keys that can be easily cracked. This is why Ledger uses a « true » RNG embedded in a secure element for its hardware wallets, ensuring optimal randomness and maximum security for your crypto assets.
Category: WalletYou may have heard the analogy—never put all your eggs in one basket. After all, if the basket breaks, say goodbye to your eggs!
The cryptocurrency equivalent of this would be sharing a fraction of your seed phrase with multiple trusted parties—a practice known as Shamir’s Secret Sharing. But as Ledger Donjon found, this analogy breaks down when applied to cryptocurrency wallets—since a single secure wallet is generally more secure than multiple weak ones.
With this CTF challenge, Ledger tasked participants with rebuilding a seed and accessing the funds it controls using just two of three required parts—essentially breaking the security offered by this implementation of Shamir’s Secret Sharing.
Although seed splitting offers some form of redundancy, it can open up additional attack vectors as shown in the CTF challenge—not to mention the potential risk of collusion.
Category: Side Channel AttackComputers often give off more information than people realize, and sometimes, this can be used to gather data that could be considered sensitive—such as private keys.
Oftentimes, the execution of a program can be measured physically. Power consumption or electromagnetic leakage can reveal information about the code that is being executed, and even about the secret data it manipulates. This is somewhat similar to rattling around a safe to deduce what is inside it based on the noise it makes.
With this CTF challenge, participants need to extract a private key from a program just by looking at its power consumption traces—inspired by what Donjon did with the KeepKey wallet.
This vulnerability highlights why all Ledger devices generate seeds within a secure element—which does not leak information and hence cannot be exploited by this kind of attack.
Category: BlockchainA blockchain typically uses a large number of different nodes to participate in the transaction validation process—by selecting pending transactions and securely adding them to blocks. To participate in this process, these nodes need to run a specific type of software, known as ‘client software’.
Some blockchains, like Ethereum and EOS, are capable of running smart contracts, which are essential self-contained snippets of code which exist on the blockchain and are automatically executed when predefined conditions are met—such as when a payment is received or after a fixed period of time.
With the blockchain CTF challenge, Donjon created a copy of the EOS blockchain containing a vulnerability. Participants were then tasked with creating a smart contract that leverages this vulnerability to take control of a node to access (fake) critical information. This type of blockchain attack challenge is rarely, if ever, seen in CTFs.
Since most nodes on a blockchain will be running the same client software, such an exploit could be used to target a large proportion of the network with potentially devastating results. This is why code audits are necessary before a client or update is made available. Donjon is currently working on the issue of blockchain node attacks.
Category: Hardware ExploitationSoftware programs run on hardware. As a result, software and hardware are mutually dependent, and this dependence can sometimes lead to vulnerabilities. Indeed, it can be possible to exploit well-written software without any vulnerabilities if the hardware it is running on is insecure.
Because of this, secure software and hardware design go hand-in-hand, since one cannot be truly secure without the other.
With the hardware exploitation CTF, participants were tasked with attacking a highly secure physical computing device, known as a hardware secure module (HSM), by leveraging a poorly secured chip to extract the secrets it contains.
Although HSMs are often considered to be the pinnacle in cryptographic security, even they can be vulnerable if their software or hardware is poorly designed. For this reason, Ledger uses only the most battle-tested certified HSMs and wrote its own custom operating system for it—known as BOLOS.
Results and prizesThe turn out for this year’s CTF was excellent. In total, more than 400 people registered for and participated in the CTF—including participants from every continent (except Antarctica!).
Overall, more than a dozen participants managed to score over 1,000 points, while this year’s top participant was able to rack up an impressive score of 4552. Of the 19 available challenges, all but one (Ghostbuster) were solved by at least one participant, and the Scissors Secret Sharing challenge was cracked by the most participants—with almost 57 successful completions.
But after three weeks of competition, much of which was neck-and-neck between some of the participants, we can at last reveal the winners:
Click here for a full list of participants and their scores. The final scoreboard for the 10 top participants is shown below:
We will be in touch with the winners shortly to arrange delivery of the prizes!
ConclusionOn behalf of the Ledger team, thank you all for your participation and for helping to make this year’s CTF a success. We had a lot of fun building it!
We want to congratulate this year’s winners, and anybody who learned something new, or managed to capture a flag, or even stepped up to the challenge by participating. We look forward to seeing you again next year for our next CTF!
origin »Bitcoin price in Telegram @btc_price_every_hour
Quantum Resistant Ledger (QRL) íà Currencies.ru
|
|