2022-5-4 07:05 |
Hacks in the DeFi world are always in the news. DeFi protocols should start using risk management rule sets and tooling already used in traditional finance, says Kate Kurbanova of Apostro.
A single vulnerability in smart contracts can cost DeFi projects millions in user funds. While technical vulnerabilities and bugs are the first attack vectors hackers search for, one can not forget about other means used to steal funds from DeFi protocols.
Formal verification, stress testing, audits and simulations – DeFi protocols have a large list of practices and tools to choose from when it comes to technical audit and thorough code check for bugs and hidden vulnerabilities.
However, even all of the above does not guarantee protocol’s safety as some vulnerabilities come from flaws in product business logic and dependency on external markets and DeFi building blocks. These are the so-called economic vulnerabilities – they require additional economic audit and are much harder to catch in general, as the space is constantly evolving, and any code upgrade can lead to new exploit possibilities.
Therefore, the DeFi security space needs to step up a notch and adopt better risk management practices to guard users and protocols alike from economic threats.
Hacks continue to loomMany protocols have suffered exploits over the years, with the most common vectors of attacks having been documented and patched up by now. Nevertheless, there are still ways to exploit the protocol by indirectly influencing the contract’s logic or the protocol’s business logic. This could be market or oracle manipulation, influencing connected protocols or continuous monitoring of possible backdoors created by code upgrades.
Exploits of such kind may use multiple protocols throughout the execution. In particular, one of the possibilities would be using flash loan attacks to manipulate the protocol’s price oracle. To understand it better, we can look into one specific example.
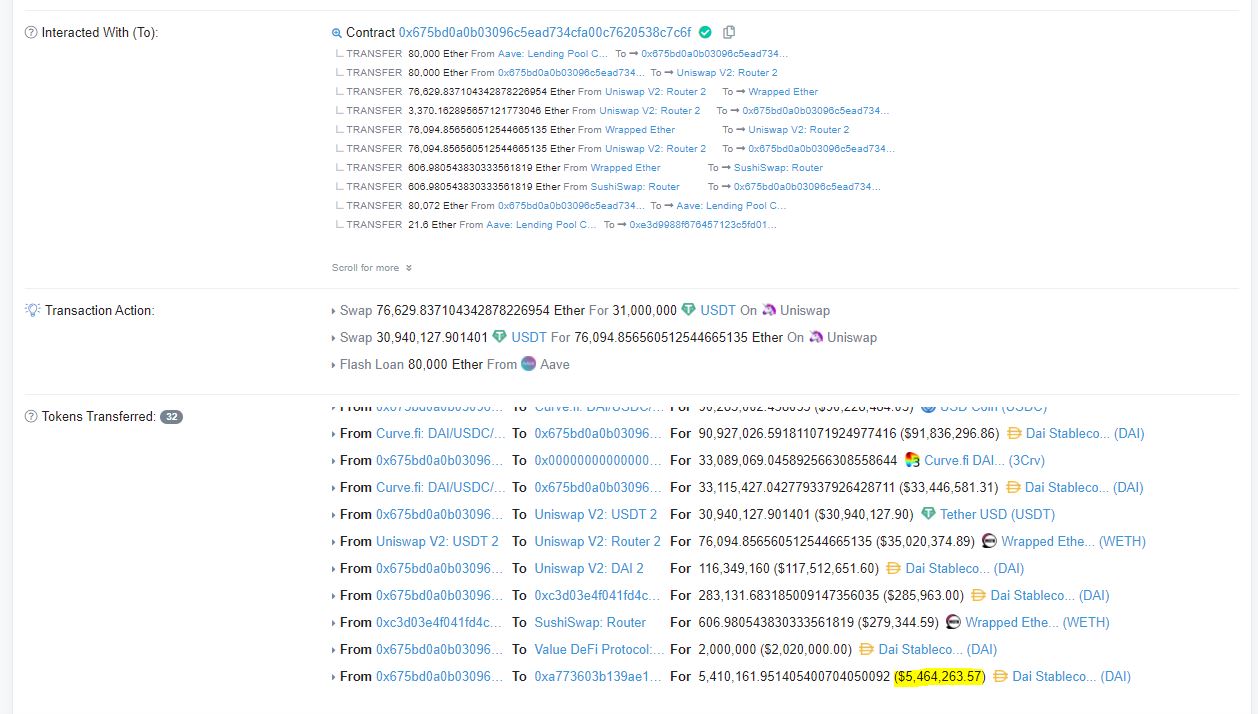
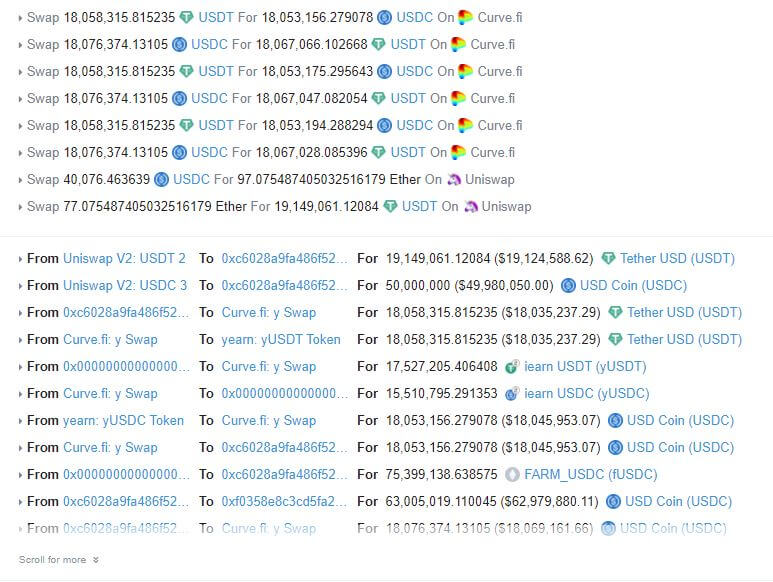
The Сream Finance ExploitThis happened back in November 2021 and resulted in a loss of $130M. The attacker manipulated the price of the yUSD by inflating liquidity and exploiting the price oracle, which led the system to believe that 1 yUSD was equal to $2, and the attacker’s initial deposit of $1.5B in yUSD had a cost of $3B correspondingly. Then the hacker converted his yUSD deposit to $3B and used $1B profit to drain all Cream Finance liquidity (~$130M).
BeanstalkAnother recent hack has used a vulnerability in the Beanstalk governance system. The hacker used a backdoor in protocol’s governance by acquiring two thirds of all governance power through flash loan. This allowed them to execute governance proposals they created with only a one-day delay (as opposed to the usual 7-day delay needed for review).
The seemingly safe proposals turned out to be a malicious contract. This activated at the time of the flash loan and essentially drained the protocol of $182 million (at the time of exploit).
Both attacks exploited the protocol’s business logic by abusing the economy behind it. These kinds of exploits show how important it is to have risk management tools and continuous monitoring in place, as they can easily catch and prevent such opportunities.
Hacks: Adopting risk management tools to enhance securityTo provide an additional layer of security against such types of attacks, DeFi protocols should start utilising risk management rule sets and tooling already proven by years of practice in the traditional finance world.
For example, one of the methods here would be implementing time-delay on transactions to the protocol. A function like that can delay suspicious transactions to the protocol, alert developers of malicious activity and give them time to mitigate the negative impact if any. This can be further improved by combining time-delay with monitoring tools to automatically delay or suspend transactions that represent threats to the protocol.
Another great practice is liquidity capping – restricting the number of funds that can be transferred in one transaction. While it won’t affect average users, liquidity capping can delay or prevent attacks similar to the Cream Finance exploit by making it more difficult and expensive for hackers to run the attack.
The DeFi security field can benefit greatly from the cybersecurity expertise of traditional finance as it would bring additional expertise and specialists to work towards higher safety and stronger infrastructure of Web3 protocols.
Hacks in DeFi: The next stepWhile the rapid growth of the DeFi sector is alluring for average users and investors alike, the lack of security practices and solutions is remaining as a major drawback for wider adoption and institutional investors.
The general audience needs more assurances when it comes to the safety of their funds – and knowledge and practices from traditional finance can push the DeFi scene to the next level of development. Adoption of risk management tooling, operational security practices, safety caps, and continuous monitoring – the DeFi sector can greatly benefit from it with the right application.
About the authorKate Kurbanova, a blockchain veteran and stock trader, is the Co-Founder & COO of Apostro. Apostro is a risk management protocol guarding against external security threats, be it a silly bug in a code or an exploit through oracle manipulation.
Got something to say about TradFi, DeFi hacks or anything else? Write to us or join the discussion in our Telegram channel. You can also catch us on Tik Tok, Facebook, or Twitter.
The post Hacks: Decentralized Finance Should Steal Ideas from Traditional Finance appeared first on BeInCrypto.
origin »Wish Finance (WSH) на Currencies.ru
|
|